I wrote a CTF challenge for the event: The Gomium Browser. Out of 10 teams 4 teams solved it (pasten, 5BC, p4, A*0*E) and a 5th team (Balsn) was really close, unfortunately their exploit was unreliable.
In this blog post I won't spoil too much and just introduce the challenge, if you'd like to try it yourself. Then in another post, I'll explain what it was all about, present my exploit and links to some of the other teams write-ups. There were some really interesting ones.
Google CTF 2019 finals
While it's still up, you can visit the Google CTF 2019 finals website:You can also see the challenges:
For Gomium we had a live event: we gave teams the challenge source code (you guessed it, written in Go) and a VM (fresh Debian 10 xfce + Go 1.13.3), then once they had an exploit ready they would put it on a USB stick and come up on stage demonstrate it live by launching xcalc on the exact same VM. Teams had only 1 try on stage, if successful we would grant them the flag but if the exploit was failed, e.g. because unreliable, they could try again after one hour.
CTF started on Saturday at 9h00 and ended on Sunday at 18h30 (all times GMT as it was happening in London). The timeline of exploit attempts:
- Saturday 14h46: successful exploit by pasten, less than 5 hours after CTF start!
- Sunday 11h30: successful exploit by 5bc
- Sunday 13h59: successful exploit by p4
- Sunday 17h00: failed attempt by Balsn
- Sunday 17h18: successful exploit by A*0*E
- Sunday 18h20: second failed attempt by Balsn
Despite trying twice on stage Balsn unfortunately did not launch calc, but I saw their exploit worked after trying it again multiple times, it was like ~20% reliable on the VM.
The challenge
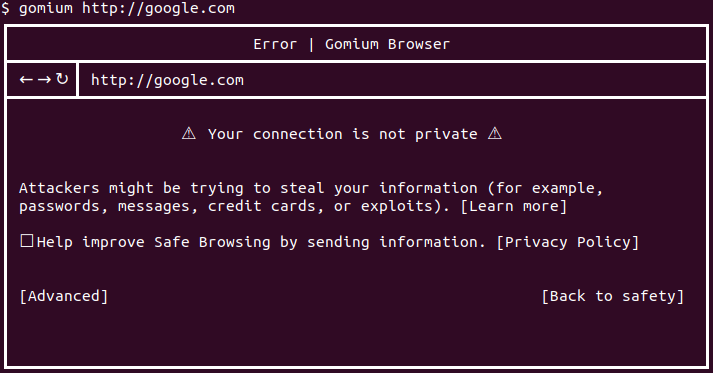
Players were given gomium.go source code (~500 lines of Go) and the VM.You can compile it with go build gomium.go, then it's a browser in command-line with an ascii-art interface and a few easter eggs:
As you'll see, the browser part is just a frame: it reads the web page, extracts Go code inside <script language="text/goscript"></script> tags, parses it, only allows the fmt package, builds it and runs it with a 5s timeout.
So the challenge boils down to answering this question: if you control Go source code but can only import the fmt package, can you get arbitrary code execution?
For the CTF we gave players a VM with a fixed Go version, things were reproducible, they could hardcode addresses, offsets, etc. But now that the CTF is over, can you make a reliable exploit, with no hardcoded addresses/offsets, and maybe even partially or completely independent of the Go build and version?






No comments:
Post a Comment